Today is International Data Privacy Day. In fact, every day should be Data Privacy day, given its relevance and the likelihood that it will be one of the widely discussed topics in the technologically dependent, post-pandemic world.
Data Privacy Day marks the signing of Convention 108, the first legally binding international treaty addressing privacy and data protection, on January 28, 1981.
The significance of data has grown in the cusp of the COVID-19 pandemic, as more and more people are required to spend time online. Millions of people still don’t understand how their personal information is used, collected, and shared. Failure to protect one’s privacy may result in exploitation and damage to a person’s finances and even affect mental health.
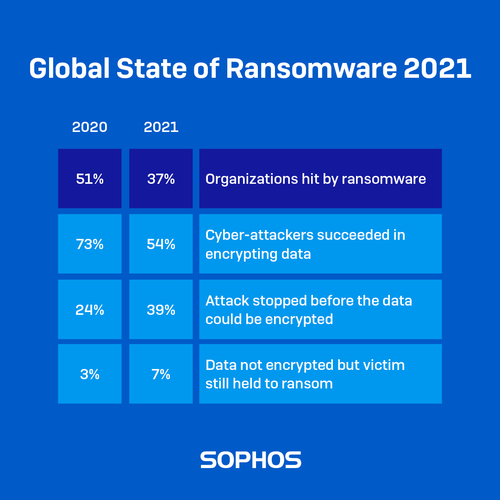
According to Sophos’ The State of Ransomware 2021 report, 51 per cent of organisations that have not been hit by ransomware but expect to be in the future believe it is because ransomware attacks are becoming increasingly difficult to defend against due to their sophistication.
Moreover, the most recent Office of the Australian Information Commissioner (OAIC) report said that 30 per cent of data breaches were caused by human error, emphasising the importance of prioritising cyber awareness within organisations.
“Because organisations have become better at protecting themselves at a technical level, attackers will hook in victims on an emotional level by leveraging fear, uncertainty, and doubt (FUD) to pressure employees to comply with their demands, Aaron Bugal, Global Solutions Engineer, Sophos tells Dynamic Business.
“It sounds simple, but awareness is key to reducing the impact of a cyberattack, no matter how robust an organisation’s cybersecurity infrastructure is.
“Once a threat finds its way through a security system, it is up to the receiver of the threat to react accordingly, which will determine whether they become a victim or an additional barrier to preventing an attack.
“It’s important that employees are equipped with the knowledge to be able to detect, identify and respond accordingly to an attack. You and your team need to be prepared so you don’t crumble under pressure because that’s what the attacker wants – using a sense of urgency to make you feel vulnerable so they can coerce you into complying with their demands.”
“Good cybersecurity hygiene practices to help protect your organisation include:
Patching early, patching often – make sure you have the latest operating system updates for your apps, devices or services
Using strong passwords – make sure your password is as unique as possible, mixing up letters, numbers and special such as “#WeL!k3Th3B34ch!#”. Using a password manager or 2FA to make it harder for scammers to crack your account
Educating employees – teach them what to look out for in terms of phishing and malicious spam and introduce robust security policies. Keeping regular backups of the most important and current data on an offline storage device. Have an incident response plan that is reviewed and updated regularly.
Being aware – the Australian government has a plethora of assets available to small and medium business owners, such as the Australian Cybersecurity Centre’s information security manual, which has what is known as the ‘essential eight’, a set of technical and procedural.
Asking for help – if you don’t have the resources to monitor your business for threats, seek the services of managed threat responsive service to help keep your network secure based on controls that an organisation can implement to help them mitigate many of the threats and calculate risk.
Carol Chris, Regional General Manager for ANZ, GBG, says that cybercriminals take advantage of the vulnerability and confusion that often accompany these scenarios.
“We’ve seen this recently with the rise of RAT-related scams in Australia, where fake websites are leading to Australians and Australian SMBs losing thousands of dollars at a time.
“Consequently, the most important thing SMBs can do today to mitigate data privacy and security risks is to remain vigilant and proactively invest in technology, solutions, and processes that can identify and defend against attacks as they are happening.
“Australians’ increasing use of digital identity throughout the ongoing pandemic is also leading to consumers becoming more comfortable with sharing their identity online out of the need of a product or service.
“While this technology is significantly increasing efficiency and access to required supplies, SMBs need to ensure they also have the right processes and technology in place to be able to confirm that a customer is who they say they are.”
2 in 3 Aussie SMEs say incidents cost them over $700,000
A recent study by Cisco found that 65 per cent of Australian SMBs experienced a cyber incident over a 12 month period between 2020 and 2021, with two out of every three incidents costing them more than $700,000.
Most small businesses cannot afford to lose this much money.
“Given the budgetary constraints most SMBs face, particularly in light of the ongoing pandemic, businesses must take a risk-based approach to cyber resilience and build the right foundation,” says Ian Yip, CEO of Avertro.
“Start by determining where your critical data is. Ensure there is a way to recover it in the event of a ransomware attack. This will typically involve regularly backing it up in some form. Mandate that only the people that need to work with this data have access and remove it for everyone else.
“Next, ensure all critical systems are regularly patched to reduce the risk of compromise. Malware regularly exploits flaws in software that have been overlooked by the developers.
“Finally, cyber education and awareness start at the top. Everyone in the company needs to know that cybersecurity is taken seriously at all levels and that the right behaviours are followed at all times. For example, a simple way to ensure the risk of phishing attacks is reduced is to remind everyone that they should never click on links in emails.”
Trust no one
Noel Allnutt, Chief Sales and Strategy Officer of Sekuro, believes that Data Privacy does not need to be overcomplicated, especially when resources are limited.
“SMBs can take their first step towards improving their data security posture by adopting Zero Trust as a key defensive stance or security framework.
“Essentially, Zero Trust is about assuming everything and everyone isn’t who you think they are until you have validated their identity – for instance, through using multi-factor authentication – then only give them access to what they need access to.
“Beyond Zero Trust, there are several small steps SMBs can take to mitigate the risk of falling victim to common cybersecurity threats.
Ransomware: To help stop ransomware, start simple. Make sure everything is patched and updated and that you have a backup strategy that covers what’s in your organisation and what’s within your organisation’s clouds. Yes, you do have to back up data that’s stored in the cloud. It’s your data, after all. Also, make sure you know how to restore when you need to.
Data Theft: When it comes to data theft, the problem with many Cloud-based apps is that they like to share and store data outside of the organisation. For example, with storage apps like Box, Dropbox and Google Drive, you’re unlikely to know what data is being sent out and to where.
There are platforms like Netskope or Zscaler that allow you to see what data is being sent out, which will minimise the possibility of data theft. Companies should also do the work to set up data classification and enforce that across their organisation.
Phishing: There are platforms and systems like Mimecast that can protect against phishing, but you also need a really strong internal education program to keep your team informed on the latest tactics used by scammers – like text or social media messages from your ‘CEO’ asking for urgent or surprise purchases.
Invest in Cloud Technology
Paul Davis, Area Vice President of ANZ at Confluent, suggests that investing in cloud technology is highly advantageous for data security and privacy.
“One of the biggest challenges businesses face today is keeping up with data privacy. With the never-ending software upgrades, patching systems, new government legislation and the evolving security threats they face, companies are always in a constant race to keep up.”
“As faster connections give rise to cloud computing, businesses can resolve security issues and stay on top of mechanisms quickly in complex and disconnected IT environments.”
“Additionally, investing in talent within the industry is often overlooked, similarly determining clear roles and responsibilities to hold people accountable and deliver the best services possible.
“Hiring a Data Protection Officer that provides strategic insight and oversees IT operations could set an organisation apart and ensure that the business stays ahead of the curve.”
Data privacy is a priority
According to the AppDynamics App Attention Index 2021, security is the number one component of a high performing’ total application experience’ for consumers.
Over 90 per cent said that their expectation of brands to keep their data secure has increased since 2020, says Gregg Ostrowski, Executive CTO at Cisco AppDynamics.
“It goes to show that brands must go above and beyond to meet their users’ expectations towards security. In this post-pandemic era, a strong security posture means organisations have the necessary processes in place to protect their applications and their business from vulnerabilities and threats,” he says.
“In a world where sensitive data is constantly at risk of being compromised by malicious actors, they must be prepared and strengthen their security posture, enabling them to predict, prevent and respond to threats.
“The DevSecOps methodology, a modern approach to software development, takes things a step further and incorporates security enhancements at the beginning of the application development lifecycle for a more proactive approach to reduce risks of threats to sensitive customer data.
“But for a DevSecOps approach to be fully effective, teams need to implement a full-stack observability solution. This approach will give them in-depth visibility into the entire IT stack, including traditional legacy systems through to new, native cloud environments and hybrid deployments. It is a vital step in the right direction.”
Data breach response drills
“With data sprawl across on and off-site network environments growing, organisations must be proactive in how they approach the security of their systems.
Conducting periodic “fire drills” is one example, testing the strength, resilience, and speed of cyber defences and disaster recovery solutions, says Paul Lancaster, Director Pre Sales Engineering at Commvault.
“Business leaders may believe they have a robust strategy to fend off and recover from attacks; however, data integrity drills can confirm if these strategies are effective, ensuring critical information is always recovery ready.
“Additionally, addressing network visibility challenges must be top of mind for IT teams and executives. As companies shift from owned data management solutions to hybrid models, systems that provide insight into assets across networks are becoming critical to help drive efficiencies and provide early warnings of any issues.
“It’s time business leaders adapt their understanding of security and recovery systems, shifting from infrastructure management to where solutions are deployed to drive outcomes for the business.”
Read about the top 10 pressure tactics used by ransomware attackers in 2021
Keep up to date with our stories on LinkedIn, Twitter, Facebook and Instagram.
